Introduction
In today’s technology-driven world, data security is of utmost importance. With the increasing popularity of containerization and microservices, Kubernetes has emerged as the go-to platform for managing and orchestrating these workloads. However, securing sensitive data within a Kubernetes cluster remains a critical concern.
Understanding Kubernetes Secrets
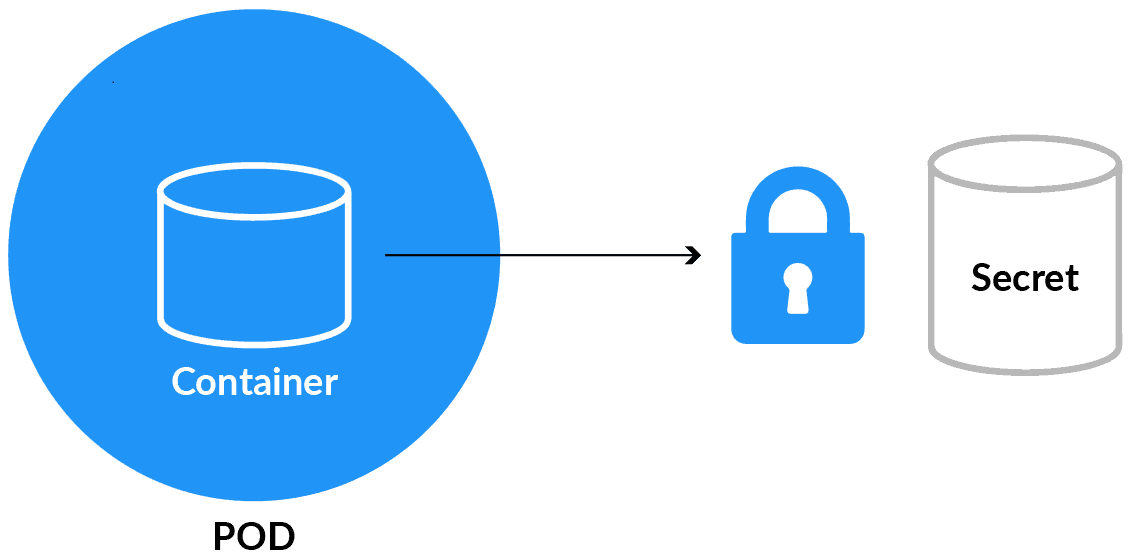
Kubernetes Secrets are a secure way to store and manage sensitive information such as passwords, API keys, and certificates. These secrets are stored within the cluster and can be accessed by authorized applications and users. By using Kubernetes Secrets, you can ensure that sensitive data is not exposed in plain text or stored insecurely.
The Problem with Hardcoding Secrets
In the past, developers often hardcoded sensitive information directly into their application code or configuration files. This approach poses a significant security risk, as the secrets become easily accessible to anyone with access to the codebase. Additionally, managing and rotating these secrets becomes a cumbersome task.
Benefits of Kubernetes Secret Storage
Kubernetes Secret Storage provides several key advantages over traditional methods of managing sensitive information:
1. Enhanced Security: Secrets are encrypted at rest within the cluster, making it difficult for unauthorized users to access sensitive data.
2. Access Control: Kubernetes allows you to define fine-grained access control policies for secrets, ensuring that only authorized applications and users can access them.
3. Centralized Management: Secrets can be easily managed and updated centrally, reducing the risk of secrets being forgotten or left unchanged.
4. Automatic Rotation: Kubernetes supports automated secret rotation, allowing you to regularly update secrets without manual intervention.
Best Practices for Kubernetes Secret Storage
When it comes to storing secrets in Kubernetes, following best practices is crucial to maintaining a secure environment:
1. Avoid Committing Secrets to Version Control: Ensure that secrets are not committed to your code repository, as this increases the risk of unauthorized access.
2. Use Strong Encryption: Encrypt your secrets using strong encryption algorithms to prevent unauthorized decryption.
3. Limit Access to Secrets: Grant access to secrets only to the applications and users that require them, following the principle of least privilege.
4. Regularly Rotate Secrets: Implement a process to regularly rotate secrets, especially in the event of a potential compromise.
5. Monitor and Audit Access: Enable logging and monitoring to track access to secrets and detect any suspicious activity.
Conclusion
Kubernetes Secret Storage plays a vital role in securing sensitive information within a Kubernetes cluster. By following best practices and leveraging the built-in capabilities of Kubernetes, you can ensure that your secrets are well-protected from unauthorized access and minimize the risk of data breaches. In the ever-evolving landscape of technology, prioritizing data security remains paramount, and Kubernetes Secret Storage provides a robust solution to address this critical need.
Configmaps Secrets Create and Update
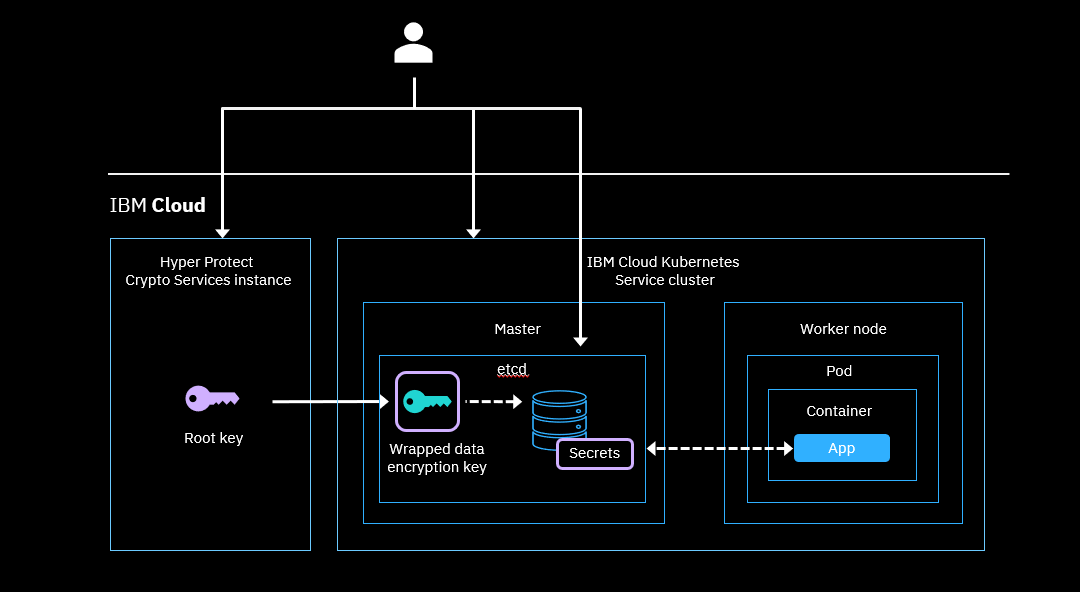
Encrypt secrets with IBM Cloud Hyper Protect Crypto Services
Sealed Secrets for How to encrypt Secret… by
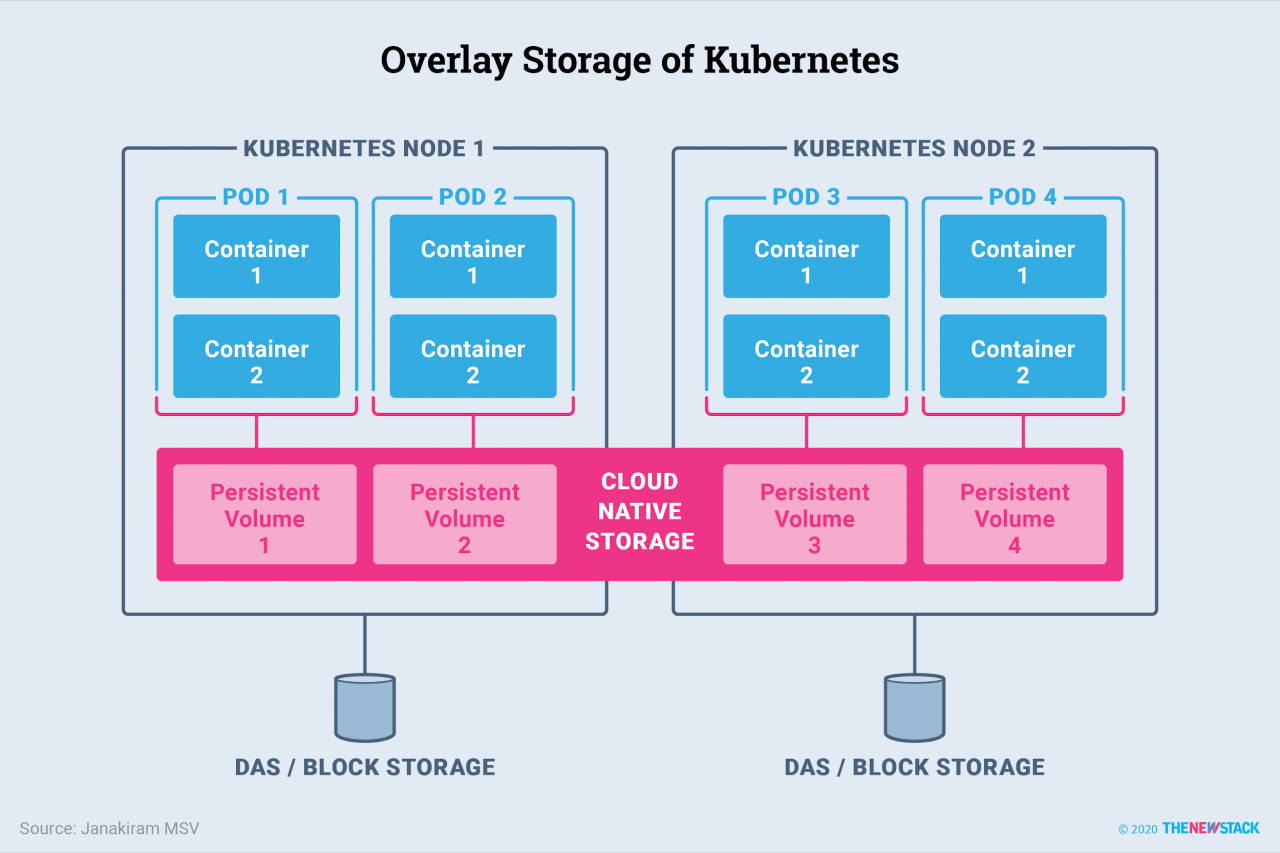
How Provides Networking and Storage to Applications The
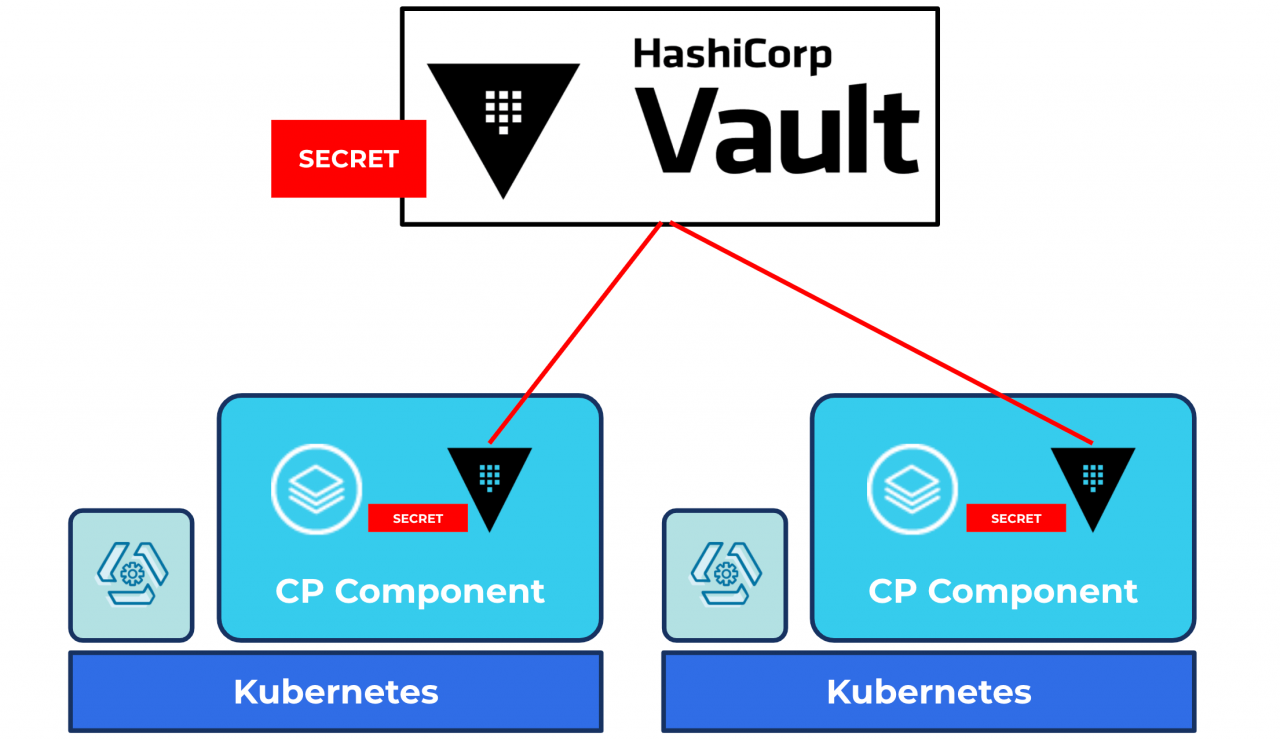
Manage Secrets for Confluent Platform with and HashiCorp Vault
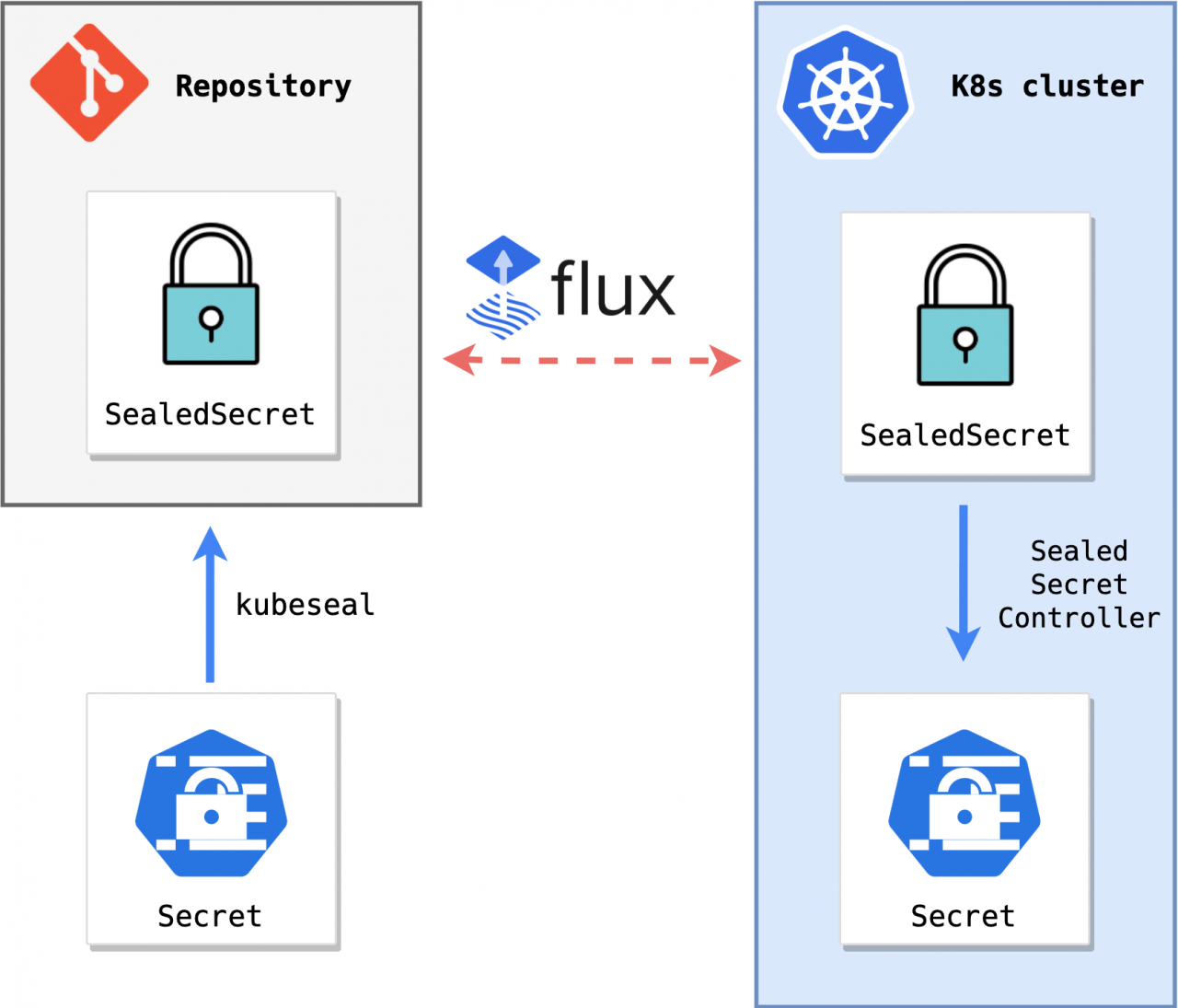
Keeping Secrets secret in Flux

Secrets How To Create, Use, and Access
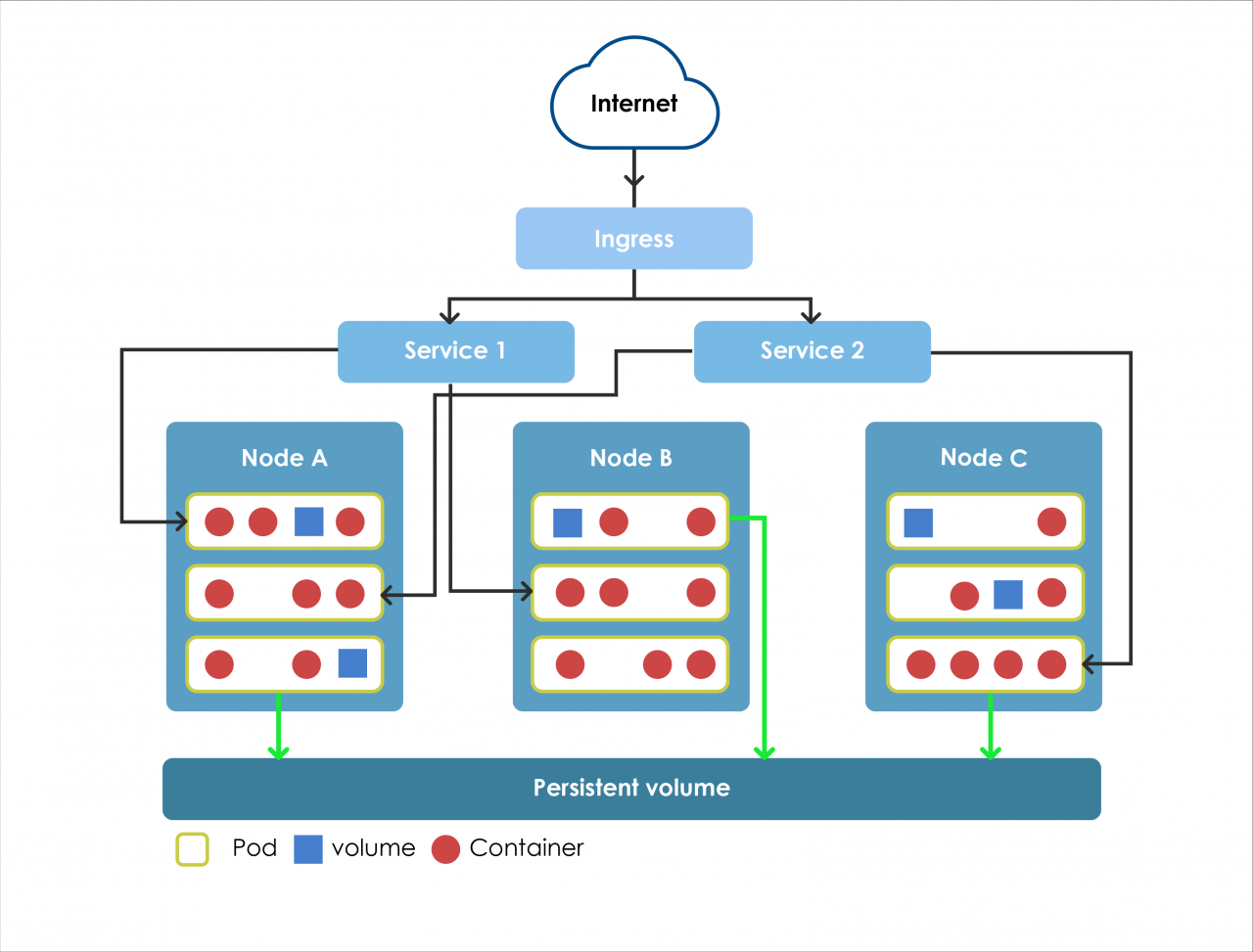
What is secrets koptiny
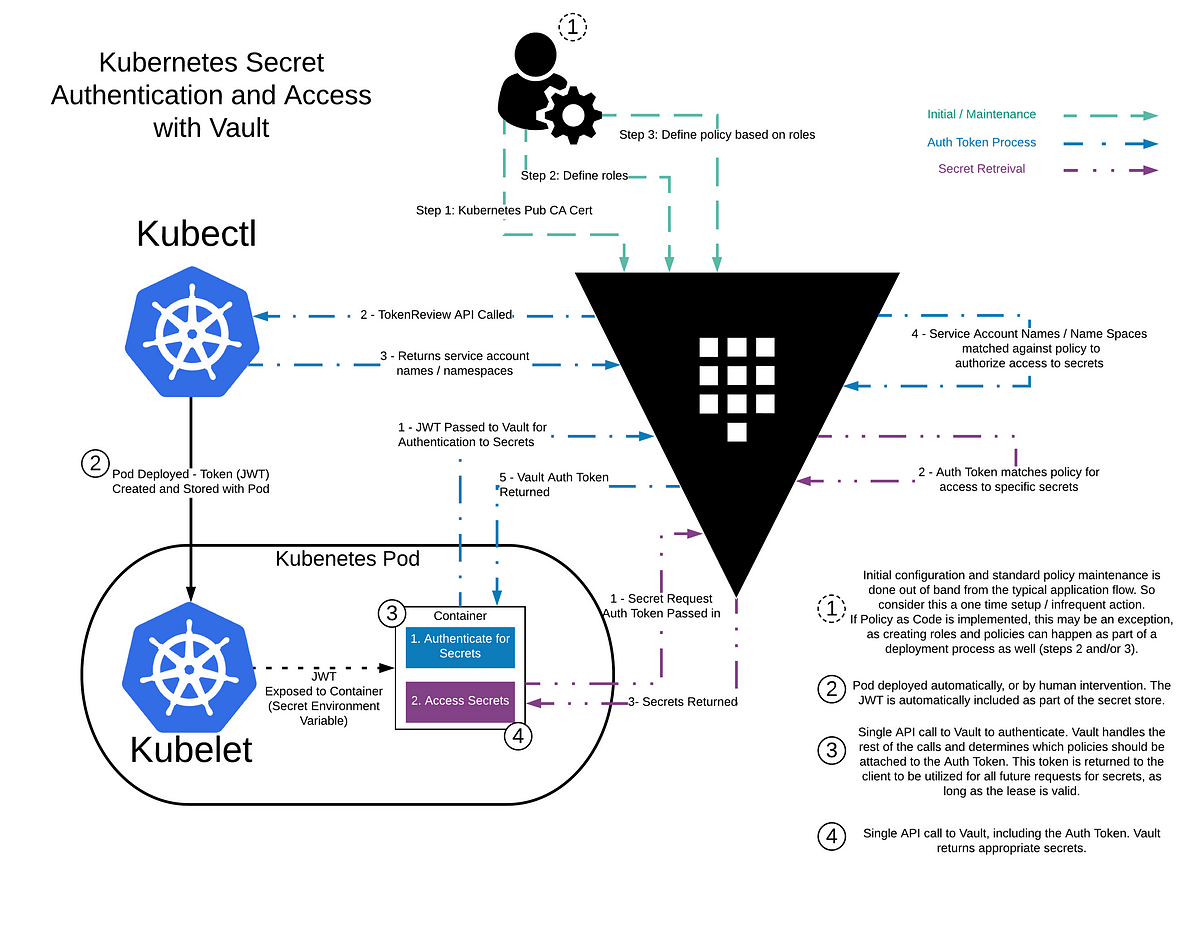
Vault setting up auth and database secrets engine by Jack

Secrets in Cloud WAF